n our previous setup we wanted one login screen for every type of authentication check. So we built a screen where you give in a Username /Password combination and press signin. We also want to support logon protocols that are used in your company, starting with Azure Active Directory. So built it that after giving your username/password combination we tried to login on Azure Active Directoy in the backgroud. This way the login screen stayed the same and your have a valid user in your Active Directory.
In hindsight this does not work. When you enable MFA (Multi Factor Authentication) or configure an STS (Security Token Service) on your Azure AD configuration, this approach doesn’t work. So we changed the login screen and removed the password field.

Picture 1: removed password field
After giving your Email, we check if you have an external account (your Azure Active Directory), or internal account (an account created within the Webdashboard). Internal account just prompts for your password and you can continue.
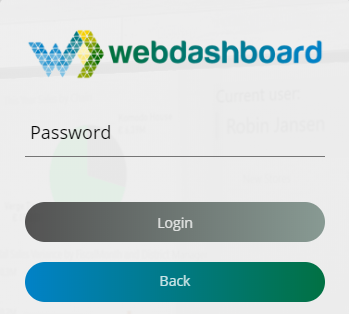
Picture 2: Internal account
When you have and External account (only Azure Active Directory is supported now) you are redirected to your STS or default Azure Active Directory login screen. Complete with MFA support, like you are used to with Azure Active Directory.
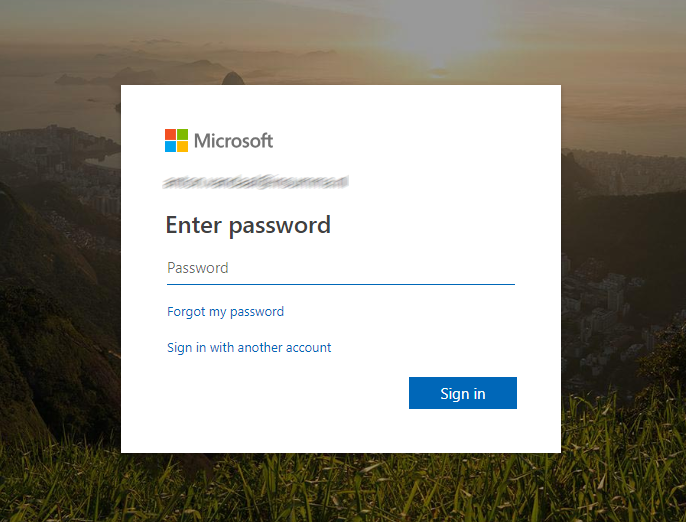
Picture 3: External account
Now every type of configuration of your Azure Active Directory is supported.